On September 6th, 2022, iThemes released a security advisory on their BackupBuddy plugin. As a global network, we’re able to actively monitor attacks in the wild as they hit our network.
This article shares what we’re seeing.
The BackupBuddy Plugin Vulnerability
The iThemes article doesn’t go into detail about the vulnerability, but describes the vulnerability as this:
This vulnerability could allow an attacker to view the contents of any file on your server that can be read by your WordPress installation. This could include the WordPress wp-config.php file and, depending on your server setup, sensitive files like /etc/passwd.
This is what we call a Local File Inclusion Vulnerability (LFI). As implied by the name, LFI vulnerabilities expose, or run, files residing on the same web server. In this instance, it appears to be a pretty serious issue if they can expose files like /etc/passwd a file that hosts user information for the server or even wp-config.php a file that houses sensitive information for WordPress like database information (including passwords). This is also the type of vulnerability to expose other information like .env files, API credentials, similar to what we reported on with our AWS Credential Harvesting article.
This vulnerability only impacts sites running BackupBuddy versions 8.5.8.0 through 8.7.4.1.
Monitoring Attacks and Other Indicators of Compromise (IOC)
They provide guidance to look for: local-destination-id, /etc/passwd, or wp-config but I would caution against the latter tool. The passwd is one of the most sought-after files on the web server and there are a lot of LFI vulnerabilities that are being actively scanned for daily.
Here is a better example of what to look for:
perezbox.com cdn-edge-canada-montreal1 198.27.68.131 200 783 - waf:js_challenge 08/Sep/2022:23:29:09 +0000 "GET /wp-admin/admin-ajax.php?local-download=wp-config.php&local-destination-id=0 HTTP/1.1" "-" "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.125 Safari/537.36"The interesting attack payload is here:
admin-ajax.php?local-download=wp-config.php&local-destination-id=0You might also see attacks targeting admin-post.php with the same attack structure.
Analyzing our logs, we’re able to confirm attacks starting sometime around August 27th:
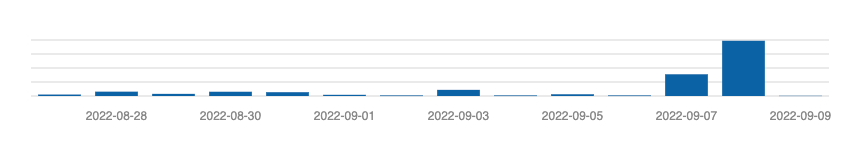
At its peak yesterday we were recording 4k attempts against various sites on our network. They ramped up on the 7th / 8th as to be expected with the release of the security notice. This only highlights the importance of speed when it comes to pushing security updates to your applications. If speed is not an option, leveraging cloud-based solutions that can help protect you at the edge via a Website Application Firewall (WAF) is advised.
Using our Trunc logging platform we ran a quick query to find all the offending IPs. It’s been isolated to about 118 IPs, but that will likely grow:
search "local-destination-id" |tail -n 2000 | cut -d " " -f 2 | sort -u -r
268, 195.178.120.89
58, 46.253.243.143
45, 20.229.10.195
43, 195.201.195.185
25, 176.31.226.16
24, 51.254.101.7
23, 51.210.134.180
22, 51.161.197.85
20, 103.57.222.214
19, 62.171.137.109
18, 159.203.5.240
17, 104.151.59.173
17, 185.92.149.129
17, 216.127.171.235
16, 92.204.239.23
16, 92.204.239.129
14, 51.68.140.110
13, 57.128.19.205
12, 128.199.105.215
12, 194.163.163.116
12, 51.159.97.30
12, 165.227.60.12
12, 20.203.211.184
10, 135.125.234.210
10, 74.208.19.189
10, 167.172.166.178
10, 185.190.140.51
10, 37.187.77.228
10, 51.210.111.136
10, 104.248.124.41
9, 52.69.222.152
9, 87.98.173.192
8, 51.75.123.243
8, 92.204.239.50
8, 192.241.184.30
8, 167.99.143.63
8, 46.182.4.117
7, 144.126.131.130
7, 88.99.35.48
6, 82.165.97.118
6, 167.71.239.218
6, 192.81.211.161
6, 162.244.33.54
6, 144.217.87.198
6, 206.189.201.198
6, 85.214.141.230
6, 92.51.146.77WordPress Security – Supply Chain Threats
In the larger security ecosystem, there has been a growing conversation around the importance of security within the supply chain. WordPress, like many systems, has its ecosystem and supply chain. We have seen this same instance play out time and time again. The thing that makes WordPress insecure is not WordPress itself, but it’s the thing that makes it so powerful – its extensibility. Plugins, themes, etc are all pieces of the WordPress supply chain ecosystem.
Over the next few years, the larger InfoSec pressures and discussions will find themselves in WordPress, other CMS, ecosystems and we will all want to start preparing ourselves for the bigger conversation of, “Security the WordPress Supply Chain”.
This instance is a perfect example of a Supply Chain problem in WordPress and we commend Backup Buddy for its focus on creating a safe ecosystem by forgoing its subscription requirement to get the update:
We have made this security update available to all vulnerable BackupBuddy versions (8.5.8 – 8.7.4.1), regardless of your current BackupBuddy licensing status, so no one continues to run a vulnerable version of the BackupBuddy plugin.
This, however, won’t be enough. Organizations will still not update, admins will still not know of the problems, and organizations will get popped because of their inability to update the plugin.
** All NOC customers were automatically protected from this Vulnerability during the Zero Day event**
