A framework should provide the underlying structure from which we built our security governance program.
Consider a home. Regardless of the type of home, they all have a similar framework. The framework keeps the house together and defines the basic structure, it starts with the foundation on which the house will sit. From there, the developers and architects build and expand it into something that fits their specific requirements. Without a basic framework, the house will collapse, the same applies to your organization’s security program.
The security problems we face today are more often than not attributed to human behavioral problems, more so than technical ones. We invest a tremendous amount of energy into the latest technologies, deploying controls designed to mitigate risk, and yet we all continue to suffer from compromises. It’s not that the technologies don’t work, but rather that our approach is flawed; it lacks the structure required to adequately account for the emerging threats.
Attackers are successful not because we’re technically incapable, but because we are behaviorally weak. – Tony | @perezbox
Something I learned at GoDaddy / Sucuri was that the tools we built (e.g., CDN/WAF/Backups/Remediation) were one piece of a larger puzzle. It’s not that our product was ineffective, but that the businesses leveraging the products lacked a basic understanding and appreciation for basic security principles. Tools would be employed with no structure in place to define why they are being deployed.
Take into consideration the organization that deploys a Web Application Firewall (WAF) to mitigate external threats by virtually hardening and patching at the edge. Sounds fancy, right? And technically works great! Until you learn that the same organization doesn’t block direct access to the server. In other words, an attacker can access the site directly, bypassing the defensive control.
We have to do a better job of bridging the divide between the knowledge that today’s webmasters have, and those that they require to effectively manage their websites security. We do this by starting with the basics – let’s create a basic Website Security Framework that any organization, regardless of size, can employ.
A Website Security Framework Intro
The basis of this framework is not new. It’s borrowed from the Framework for Improving Critical Infrastructure Cybersecurity, developed by the US National Institute of Standards and Technology (NIST). The idea is to educate users on a framework that already exists and can be easily leveraged for your organizations website security needs.
It is built on 5 core elements: Functions, Categories, Subcategories, and Informative References. Their relationship is as follows:
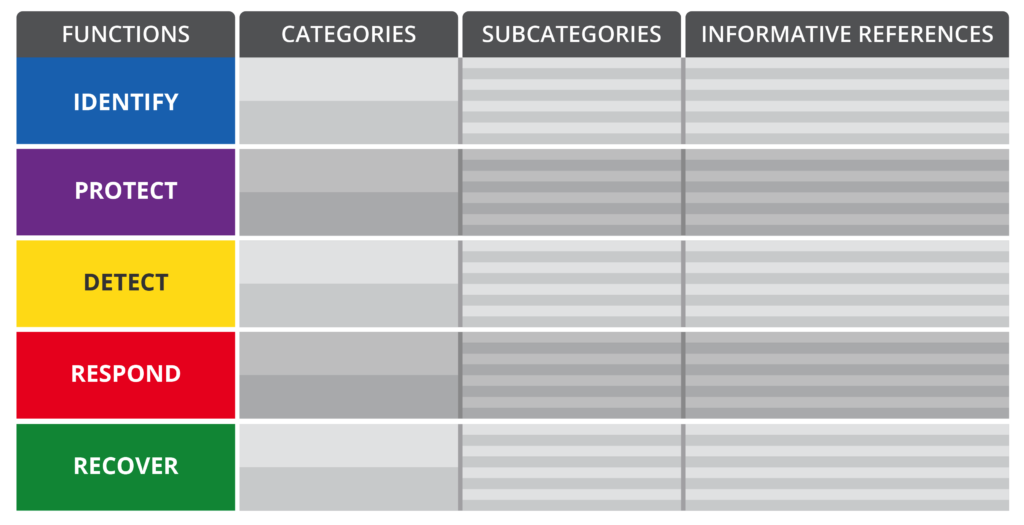
The functions are designed to organize the key security domains you should be considering. Keep the functions to these core five domains, do not over complicate.
As the illustration shows, the categories are subdivisions of the functions, and the subcategories subdivisions of categories. There is a one to many relationship between Functions and Categories, and Categories and Subcategories. The informative references have a one to one relationship with the subcategories, they are important to ensure that everyone is aligned with the exact steps being leveraged for each control and action.
Improving An Organizations Security Posture
Before deploying security solutions into your stack ask yourself what your general disposition is towards security. The framework above is designed to help you in this process.
As you consider the framework, think of security as a continuous process. The threat landscape is constantly evolving, your security posture should also evolve. Revisit the process at some interval (e.g., weekly, monthly, quarterly). It’s not about the frequency as much as the simple act of actually revisiting the process.
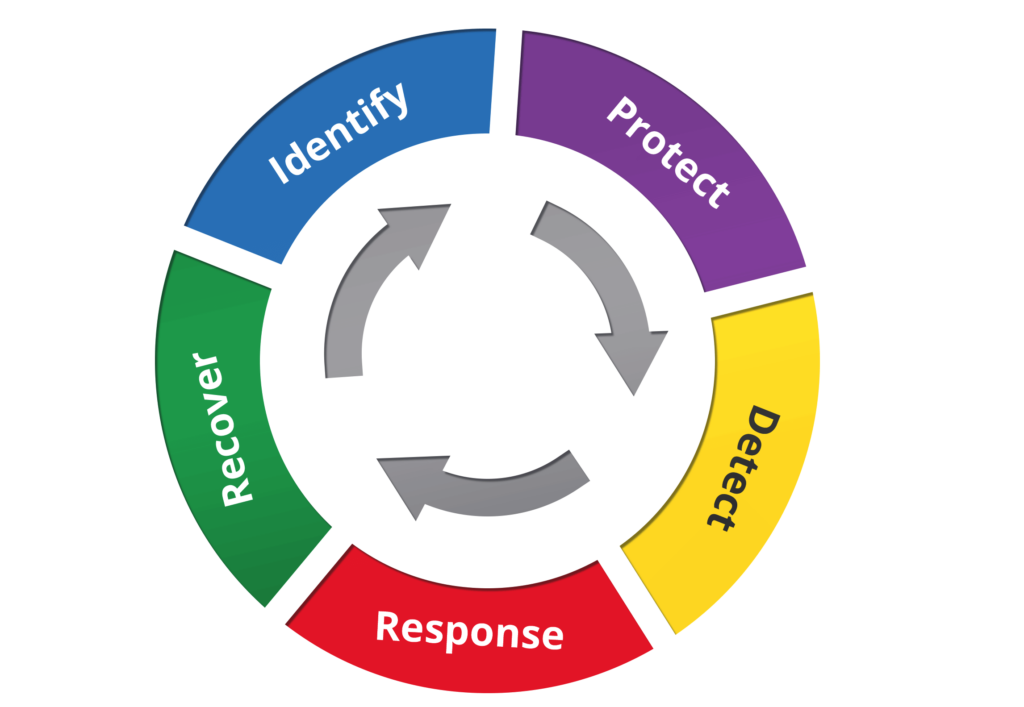
It can feel overwhelming when you first start thinking about a framework for your organization, which is why we recommend breaking it down into bite-sized chunks. The easiest, and most difficult, is always the identification step.
In my experience, rarely does an organization have a good handle on what they own. You can’t protect what you don’t know exists.
Things to consider through the process:
- When was the last time you created an inventory of?
- What is your technical stack?
- Who knows what your technical stack is?
- How many domains are part of your brand’s portfolio?
- What does the supply chain look like for your various digital assets?
- What systems/services are you dependent on?
- Where are they hosted?
- Who has access to these environments?
We do not get hacked because cyber criminals have an advantage over us, or because of the platforms we use. We get hacked because we lack basic knowledge, and in some instances we’re very complacent. We fail to take the basic precautions required when introducing a new property to the greater internet ecosystem.
