NOC WAF Protects
Against AFU
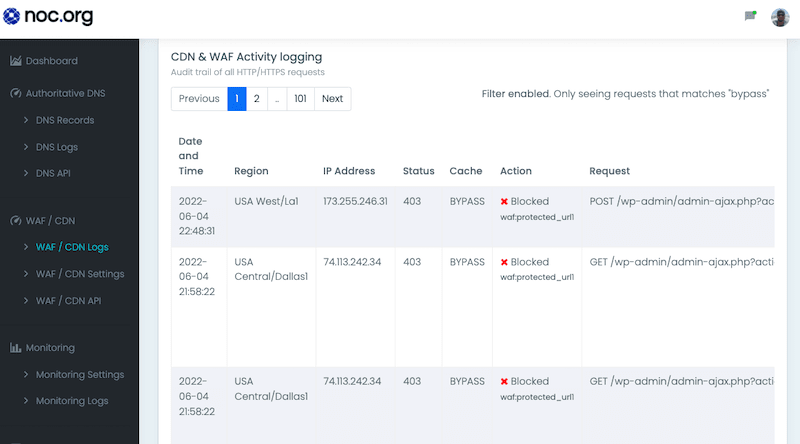
Arbitrary File Upload (AFU) vulnerabilities are vulnerabilities that allow bad actors to upload files to your server, and the NOC WAF helps protect against attacks targeting them.
**No credit card required.