NOC WAF Protects
Against XSS
Cross-Site Scripting (XSS) vulnerabilities are a fan favorite for bad actors, and the NOC WAF helps protect against attacks targeting them.
**No credit card required.Cross-Site Scripting (XSS) vulnerabilities are a fan favorite for bad actors, and the NOC WAF helps protect against attacks targeting them.
**No credit card required.
Cross Site Scripting (XSS) vulnerabilities are one of the more well-known vulnerabilities. They are similar to SQLi vulnerabilities in that they fall into a broader bucket - Injection Vulnerabilities as defined by OWASP.
XSS vulnerabilities allow bad actors to manipulate the JavaScript on a web application. There are three types of XSS vulnerabilities:
The NOC WAF is able to mitigate attacks that try to abuse XSS vulnerabilities.
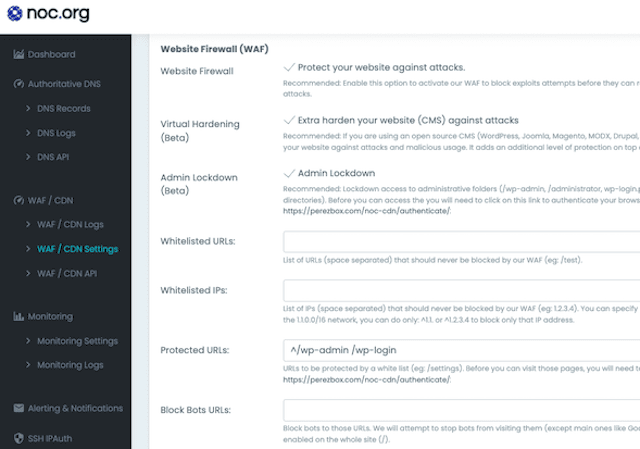
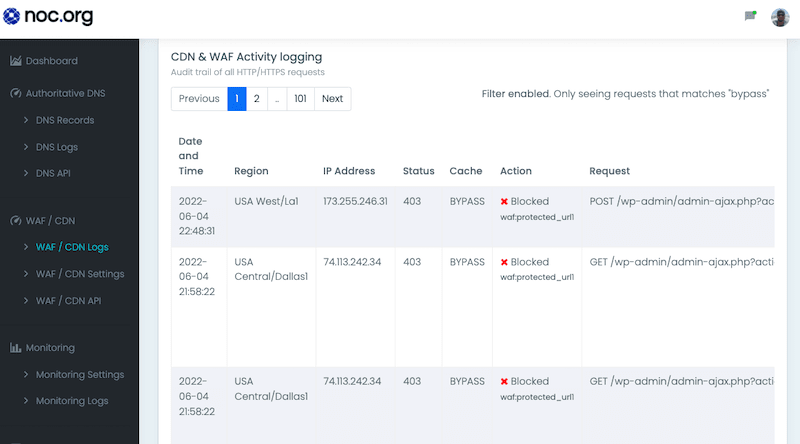
The NOC platform is unique in its proprietary Web Application Firewall (WAF) technology. This technology complements the CDN and ensures that your website is always protected.
Some features include: