The NOC platform runs a global anycast CDN/WAF with points of presence around the world. That design not only delivers great performance—it also provides visibility into attacker behavior at scale. Shortly after Apache released a security update for CVE-2021-41773, we observed a rapid uptick in probing and exploitation attempts.
If you’re unfamiliar: on October 6, 2021, Apache shipped patches for 2.4.50 (and 2.4.49) to address a path traversal vulnerability later tracked as CVE-2021-41773. All NOC customers using our Web Application Firewall (WAF) received virtual patching coverage by default.
What the Exploit Looks Like
This vulnerability allows attackers to map URLs to files outside the expected document root via path traversal. If those files aren’t protected (e.g., by Require all denied), requests can succeed and even leak source of interpreted files (like CGI).
We observed requests like the following on our edge:
cdn-edge-europe-london1 88.168.206.87 400 129 - waf: 08/Oct/2021:05:26:09 +0000 "GET /cgi-bin/.%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd HTTP/1.1" "-" "-"
cdn-edge-europe-london1 88.168.206.87 400 129 - waf: 08/Oct/2021:05:26:35 +0000 "GET /cgi-bin/.%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd HTTP/1.1" "-" "-"
Each request attempts to access /etc/passwd outside of the webroot using URL-encoded traversal (.%2E/%2E%2E → ../). Decoded, it looks like:
/cgi-bin/../../../../../../../../../../etc/passwdActivity in the Wild
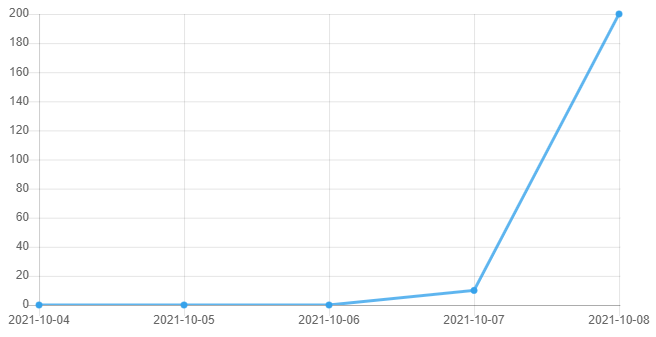
We saw light reconnaissance on October 7 followed by heavier scanning and exploitation attempts soon after. Below is an illustration focused on requests targeting this CVE:
Why Cloud WAF + Automation Matter
Vulnerabilities that can be exploited remotely through your apps are where cloud WAF shines: immediate virtual hardening without production changes or maintenance windows. Your hosts will patch on their cadence; your WAF can protect now.
If you run Apache, update to the latest version. As an additional hardening measure, apply strict directory access controls (e.g., Require all denied) for sensitive paths.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans