Software Bills of Materials (SBOMs) have surged in popularity as organizations grapple with the impact of vulnerabilities in open-source components. The idea isn’t new—its roots are in traditional supply-chain management—but the adaptation to software finally has momentum and regulatory backing.
Tackling Supply-Chain Vulnerabilities
The need for SBOMs is driven by visibility. Incidents like Log4Shell and past high-profile flaws (e.g., Apache Struts in the Equifax breach) showed how dependencies buried deep inside stacks can become organization-wide risks. Even maintainer actions—like a developer intentionally corrupting a popular library—have rippled across the ecosystem.
Public-private efforts are pushing standards forward, and in the U.S. Executive Order 14028 put particular emphasis on securing software supply chains. SBOMs are becoming a cornerstone of that strategy.
Open-Source CMS Are Supply Chains, Too
Open-source CMS platforms (WordPress, Drupal, Joomla, Magento, and others) power a huge portion of the web. They don’t just consume supply chains—they are supply chains. Each site is a composition of core, themes/designs, plugins/modules, and third-party services. That extensibility is a strength for building, but a weakness for security when visibility is poor.
Side note: We’d like to see more representation from major CMS communities in national cybersecurity initiatives. These platforms are as foundational as system-level projects like Linux, OpenSSL, Apache, and NGINX.
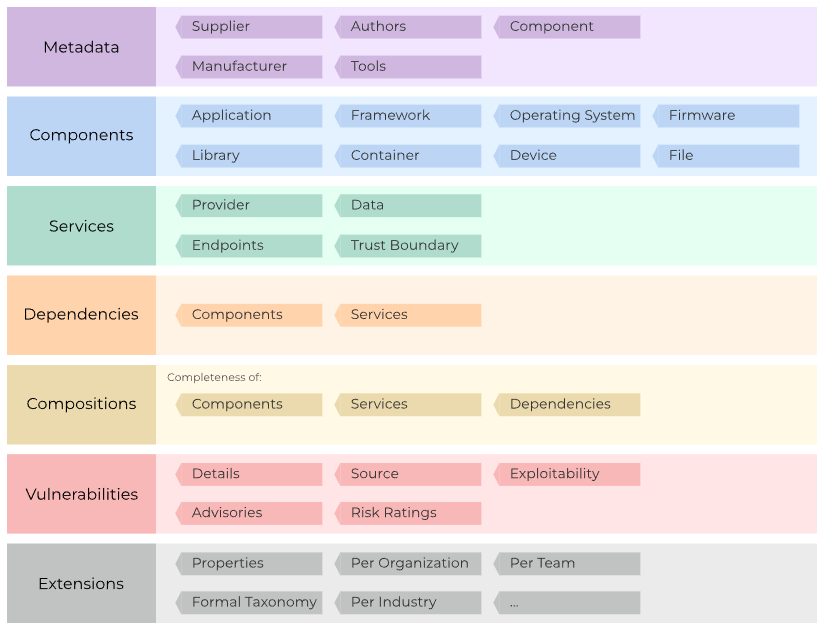
SBOM Frameworks You Can Use Today
Communities don’t need to start from scratch. The OWASP CycloneDX project provides a mature SBOM specification and tooling. It’s a strong base for CMS ecosystems to standardize how they describe components, versions, and relationships—so enterprises can ingest and reason about risk.
Practical Benefits for CMS Operators
- Faster impact analysis: Know which sites use a vulnerable component and where.
- Compliance readiness: Meet customer and regulator expectations with standardized SBOMs.
- Sane patching: Prioritize based on exposure, version, and reachability—not guesswork.
- Better vendor hygiene: Hold theme/plugin providers to clear transparency expectations.
Getting Started
- Adopt CycloneDX for your component list and automate generation in CI/CD.
- Track SBOMs alongside releases for core, themes, and plugins/modules.
- Feed SBOMs into your vulnerability management and inventory systems.
- Establish policies for third-party components (minimum maintenance, update cadence, SBOM availability).
SBOMs won’t eliminate vulnerabilities, but they turn unknown unknowns into known, trackable dependencies. For CMS ecosystems, that’s a major step toward sustainable security maturity and user trust.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans