Over the past decade we’ve helped countless organizations respond to security incidents around the world. A common theme emerges: outside of large enterprises with established security teams, most small and mid-sized businesses don’t know where to start.
This guide distills lessons we’ve learned into practical steps you can use during your most vulnerable moments. It’s written primarily for SMBs, but micro-businesses will also find value.
Who this is for
| Total Revenue | $1M – $20M |
| Total Employees | < 250 |
| CISO / Security Leader | No |
| Dedicated Security Team | No |
Incident Response Foundation
The key to responding effectively is having a simple foundation to operate from. When you first realize you’ve been compromised, emotions run high. A lightweight framework helps you stay rational.
Start by asking (and re-asking) these questions:
| What is the scope of the compromise? | Scope guides response and stakeholders. You won’t know everything up front—assume scope will evolve as you learn more. Sometimes it’s smaller than feared; other times it’s bigger. |
| Who is taking ownership? | If everyone leads, no one leads. Assign roles and responsibilities early. Who makes decisions? Who coordinates updates? Executives are key stakeholders—not necessarily the operators in charge. |
| What is the communication cadence and medium? | Decide where and how updates happen (e.g., Slack/Teams channel, incident email list) and how often (every 30–60 minutes). Make it predictable so teams can focus. |
Incident Response Work Streams
Once an incident is confirmed, it’s “all hands” for teams that can make a difference. Appoint an incident lead to shield operators from thrash and keep stakeholders informed. They’ll orchestrate parallel work streams across business functions.
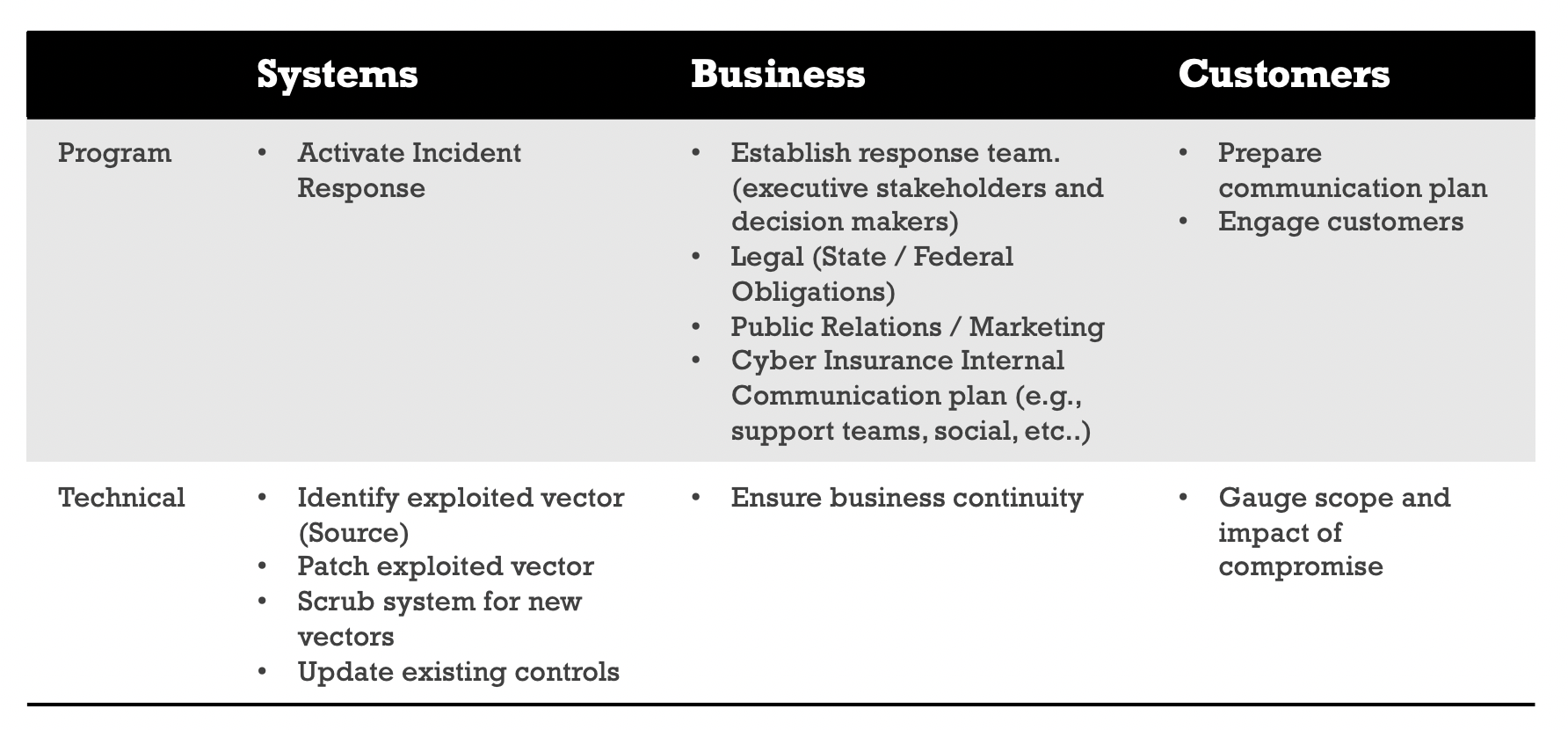
This outline isn’t exhaustive. Adapt it to your reality. The point is to provide a starting structure any organization can use.
It’s OK to run streams in parallel
Most activities can proceed concurrently. For example, communications can split into internal vs. external tracks. While technical teams investigate, comms can pre-draft best/worst-case artifacts to accelerate approvals later.
Security Breach Notification Laws / Rules
Regulations vary by jurisdiction and industry. Understanding scope is critical to knowing who you must notify (and when). In the United States, every state has its own breach notification laws—see the National Conference of State Legislatures for a current summary.
Consider your regulatory environment as well (e.g., PCI DSS, HIPAA, ISO 27001, FISMA, etc.). When in doubt, consult counsel experienced in incident and privacy law.
Incident Handling
You can’t capture every nuance in a single article. Our preferred reference is NIST’s Computer Security Incident Handling Guide (SP 800-61r2) , which frames response in four phases:
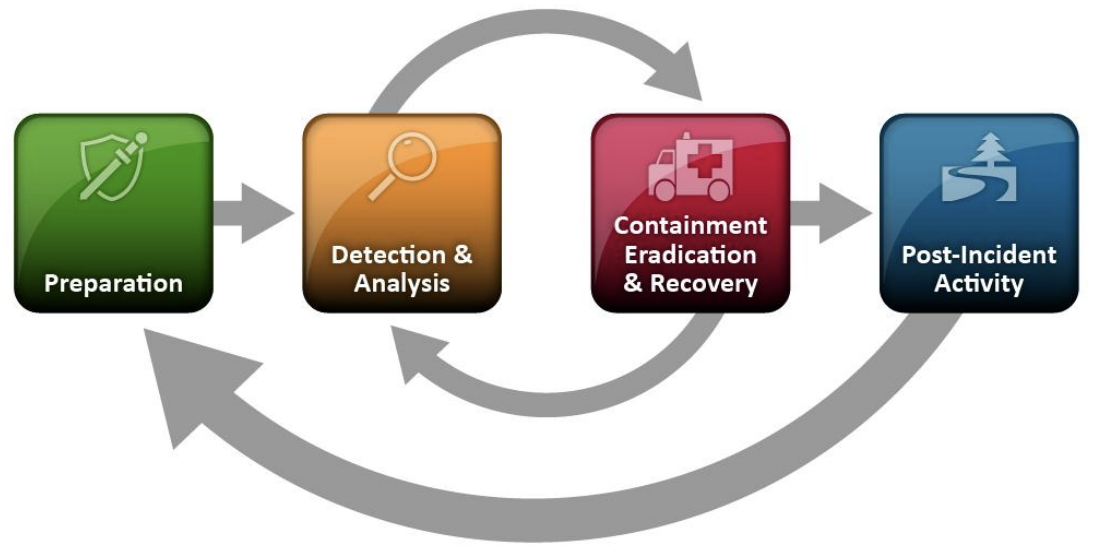
We like this model for its simplicity and its emphasis on continuous improvement. Post-incident learning is how your program matures.
The Chaos of Incidents
In every incident we’ve handled, there’s a moment of dismay. It often happens at 2 a.m. or right before a holiday. You’ll feel frustrated by gaps in telemetry, mistakes made, or actions not taken. Secret: you will never have “enough” information.
That’s normal. Use this framework to lead calmly, communicate clearly, and recover faster.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans