By default, most open-source applications expose the administrative panel to the world. From a security perspective, this design leaves a lot to be desired. It’s the #1 abused vector used to compromise sites—and the reason is simple: website owners are often poor administrators by default.
Open-Source Administrative Panels
By “admin panel,” we mean the page where you log in to manage your site. Common defaults include:
- WordPress —
/wp-adminor/wp-login.php - Joomla! —
/administrator - Magento —
/magento/admin(or a custom path) - Drupal —
/admin
Exact paths may vary by version and configuration.
These paths are common knowledge for both good and bad actors. It’s why you see patterns like this:
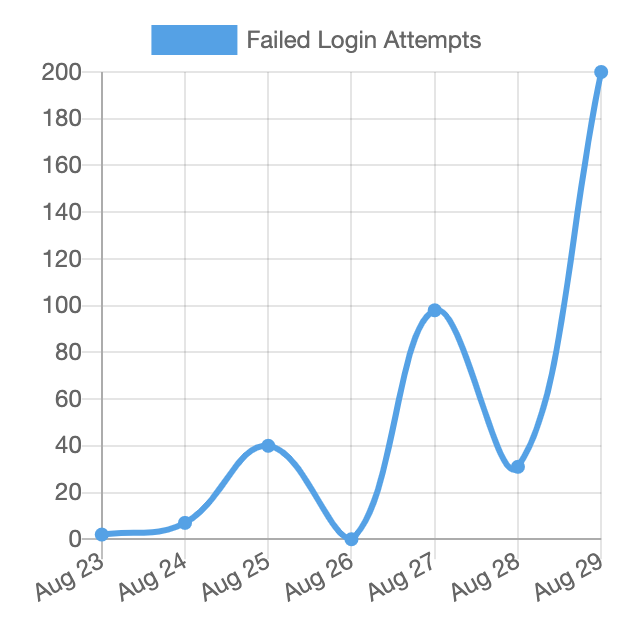
The example above (via Anthony D. Paul) shows sustained brute-force login attempts against WordPress. Odds are high it’s automated. If you analyze the POST requests, you’ll likely see boilerplate payloads. Once bots detect your CMS, they hammer the default login URL.
Root cause: the admin panel is exposed to the entire internet by default.
Protecting Admin Panels
Despite being the top abused vector for more than a decade, many owners resist restricting admin access. The reasons usually fall into three buckets:
- “We run a community; everyone needs to log in.”
- “I travel a lot; maintaining a whitelist is annoying.”
- “Multiple editors work from anywhere; we can’t lock it down.”
The community use case is the most challenging—ideally, you’d separate member authentication from the primary admin endpoint. For most sites, the single most effective hardening is to enforce a default-deny allowlist on the admin panel.
This outperforms rate-limiting, login attempt throttling, and IP blacklists. Attackers have more time, nodes, and payloads than site owners have patience. You can’t abuse what you can’t reach.
Two practical approaches:
- IP allowlisting: Permit only trusted IPs or networks.
- Browser authentication: Gate the admin path behind an additional auth layer.
At NOC, we offer browser authentication. If you try to access noc.org/wp-admin, you’ll see:
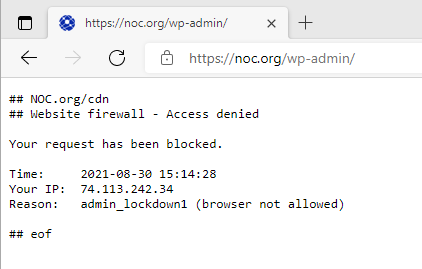
Only approved users can pass. Managing access is simple: the platform issues an authentication URL you save as a bookmark. When you need access, click the bookmark to get through.
Benefits of Hardening Administrative Panels
Beyond blocking brute force attacks, admin hardening can mitigate vulnerabilities that rely on reaching the admin area. A few historical examples:
- MailPoet (2014) — MailPoet Vulnerability Exploited in the Wild – Breaking Thousands of WordPress Sites
- Reflected XSS in plugin admin pages (2020) — affecting multiple plugins
- Duplicate Page plugin SQLi (2019) — Sucuri write-up
Harden once, benefit repeatedly—especially against automated threats. Questions about your deployment? Reach us at support@noc.org.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans