Every year, Verizon publishes the Data Breach Investigations Report (DBIR), a widely referenced snapshot of the threat landscape. At NOC, we pay special attention to the vectors abused in confirmed incidents. In 2020, the leading vector was the organization’s web ecosystem—websites, web applications, endpoints, and web servers.
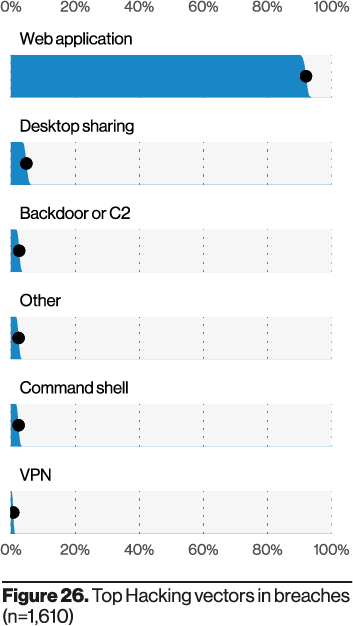
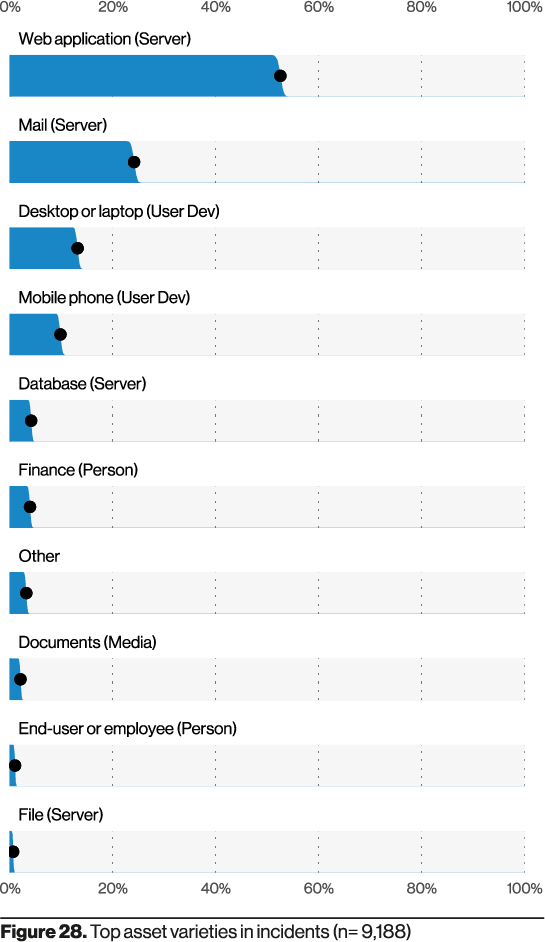
Another notable pattern is the prevalence of servers, particularly web servers, in breach scenarios.
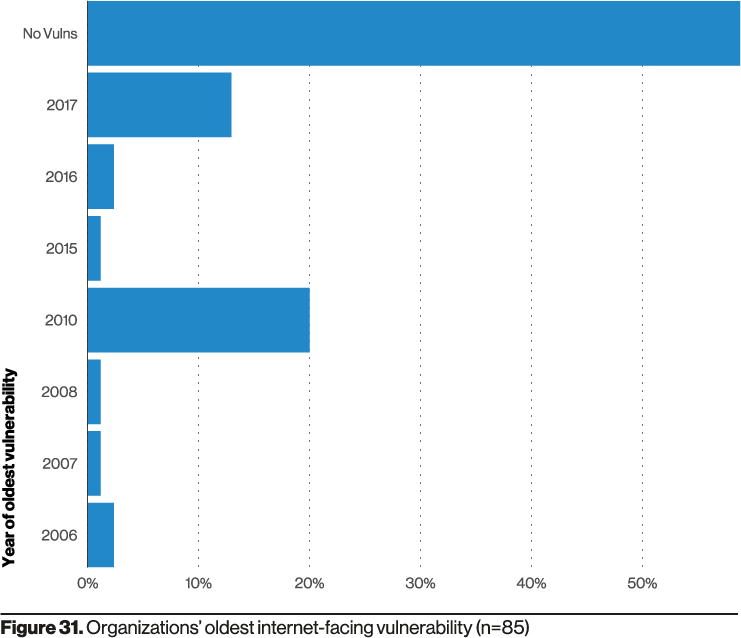
If web applications are the top vector, it’s natural to assume that software vulnerabilities explain most cases. The 2021 DBIR nuance is useful: over 50% of impacted applications had no known vulnerabilities; and when vulnerabilities were present, many were old (circa 2006–2017).
Verizon’s honeypot data reinforces this: a large share of probing targeted older CVEs—many from 2017, with some attempts dating back to the late 1990s.
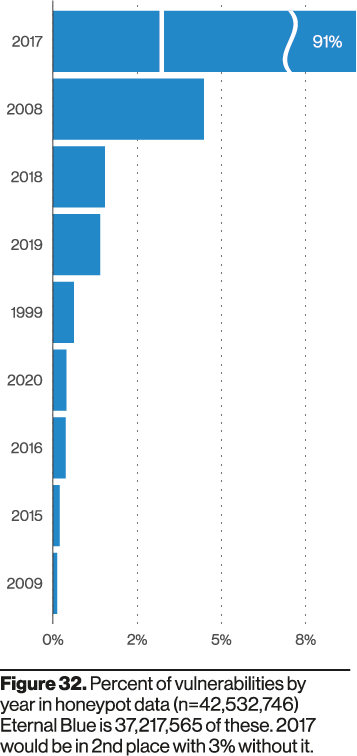
These older vulnerabilities are what the attackers continue to exploit
Source: Verizon DBIR 2021
An Organization’s Web Ecosystem
For practitioners, none of this is surprising. The network perimeter has eroded, forcing more systems to be public-facing. Business velocity demands platforms that trade simplicity for exposure (e.g., CMSs). More detail on the specific web app types would help, but the trend line is clear.
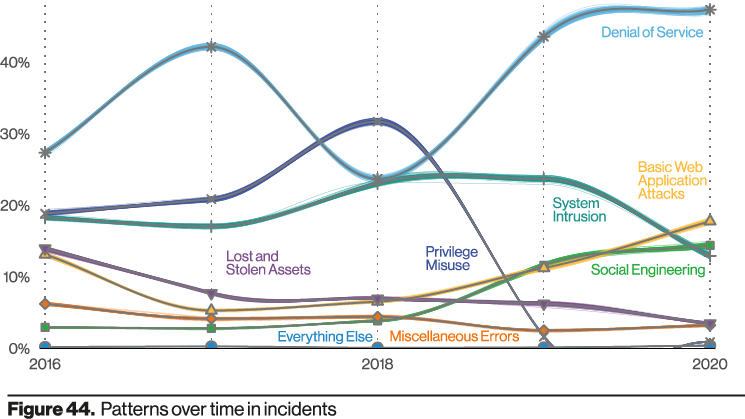
Combine that with limited funding, staffing, and time, and attackers find a sweet spot: old, unpatched vulns and weak access controls. The DBIR emphasizes smarter patching and vulnerability prioritization. In practice, organizations often also need compensating controls like a Web Application Firewall (WAF) to provide virtual patching and request hardening—especially where change management introduces weeks (or months) between discovery and deploy.
Knowing a vulnerability exists doesn’t necessarily mean the organization can patch it immediately. A WAF that offers virtual hardening and patching helps bridge that gap.
Source: Tony Perez | NOC
The report doesn’t break down the exact app types (sites vs. APIs, etc.) nor all exploitation methods. Given that ~50% of affected apps had no known vulns, a significant portion likely stems from access abuse (e.g., credential stuffing, weak auth) alongside legacy CVEs.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans