A framework should provide the underlying structure from which we build a security governance program. Think of a home: the framework (foundation, framing) holds it together and defines the basics. Without it, the house collapses. The same applies to your organization’s security program.
Many of today’s security problems stem from behavioral gaps, not just technical ones. We deploy tools and controls but lack the structure to apply them effectively to emerging threats. The result is continued compromises despite investments in technology.
Attackers are successful not because we’re technically incapable, but because we are behaviorally weak. — Tony | @perezbox
A lesson from GoDaddy/Sucuri: tools (CDN/WAF/Backups/Remediation) are only part of the puzzle. Without a basic framework, tools get deployed without clarity of purpose. Example: a WAF virtually hardens at the edge, but if direct access to origin isn’t blocked, attackers can bypass the control entirely.
Let’s bridge that gap by adopting a simple Website Security Framework any organization can use.
A Website Security Framework Intro
This framework borrows from NIST’s “Framework for Improving Critical Infrastructure Cybersecurity.” The goal is to leverage an established structure for website/security teams.
It’s built on core elements—Functions, Categories, Subcategories, and Informative References—related as follows:
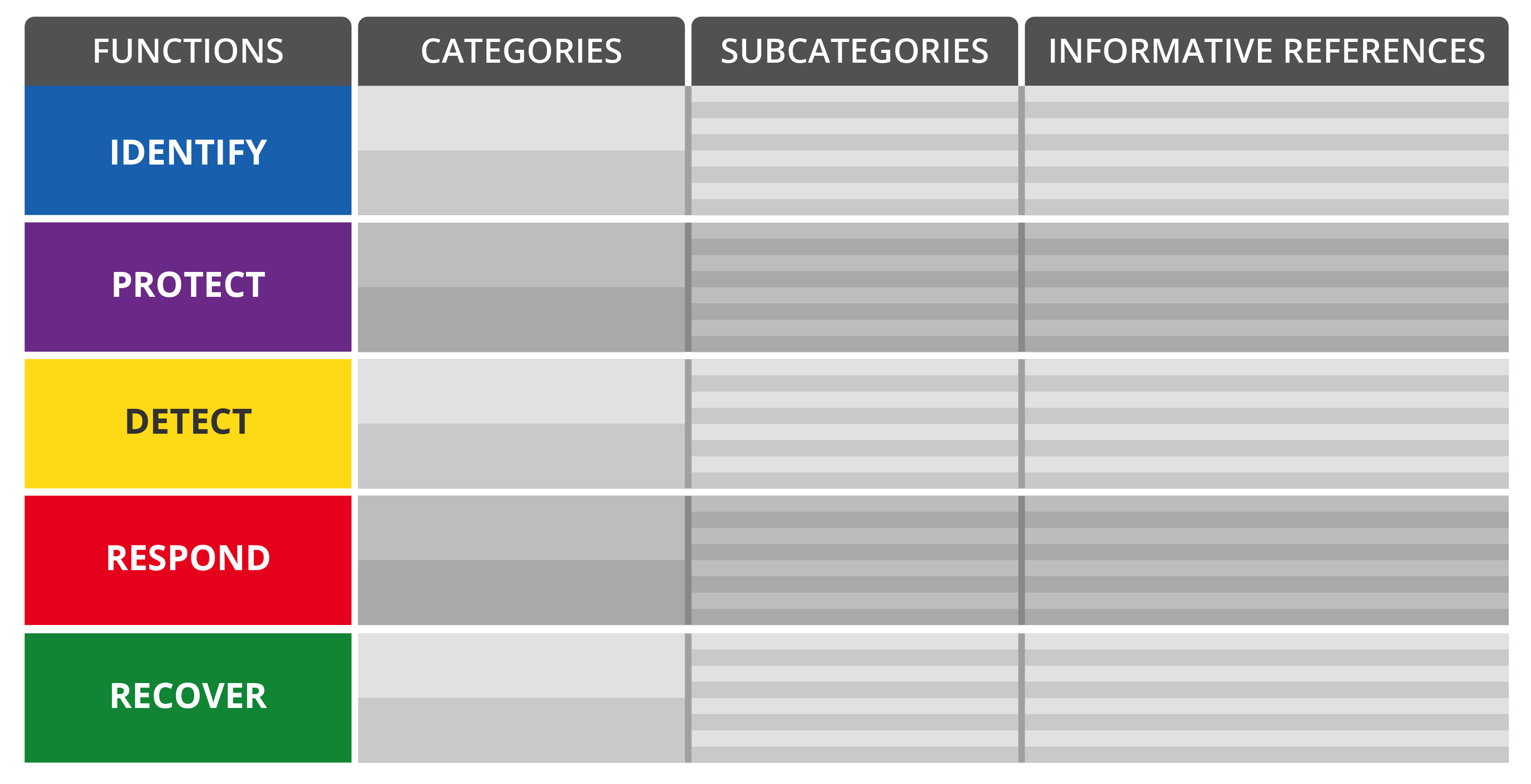
Keep the Functions focused on the five core domains (Identify, Protect, Detect, Respond, Recover)—don’t overcomplicate. Categories subdivide Functions; Subcategories subdivide Categories. Informative References map one-to-one to Subcategories, aligning teams on the exact controls/actions.
Improving an Organization’s Security Posture
Before dropping new solutions into your stack, assess your overall disposition toward security. Treat security as a continuous process: the threat landscape evolves, so your posture must, too. Revisit on a cadence (weekly, monthly, quarterly)—the key is consistency.
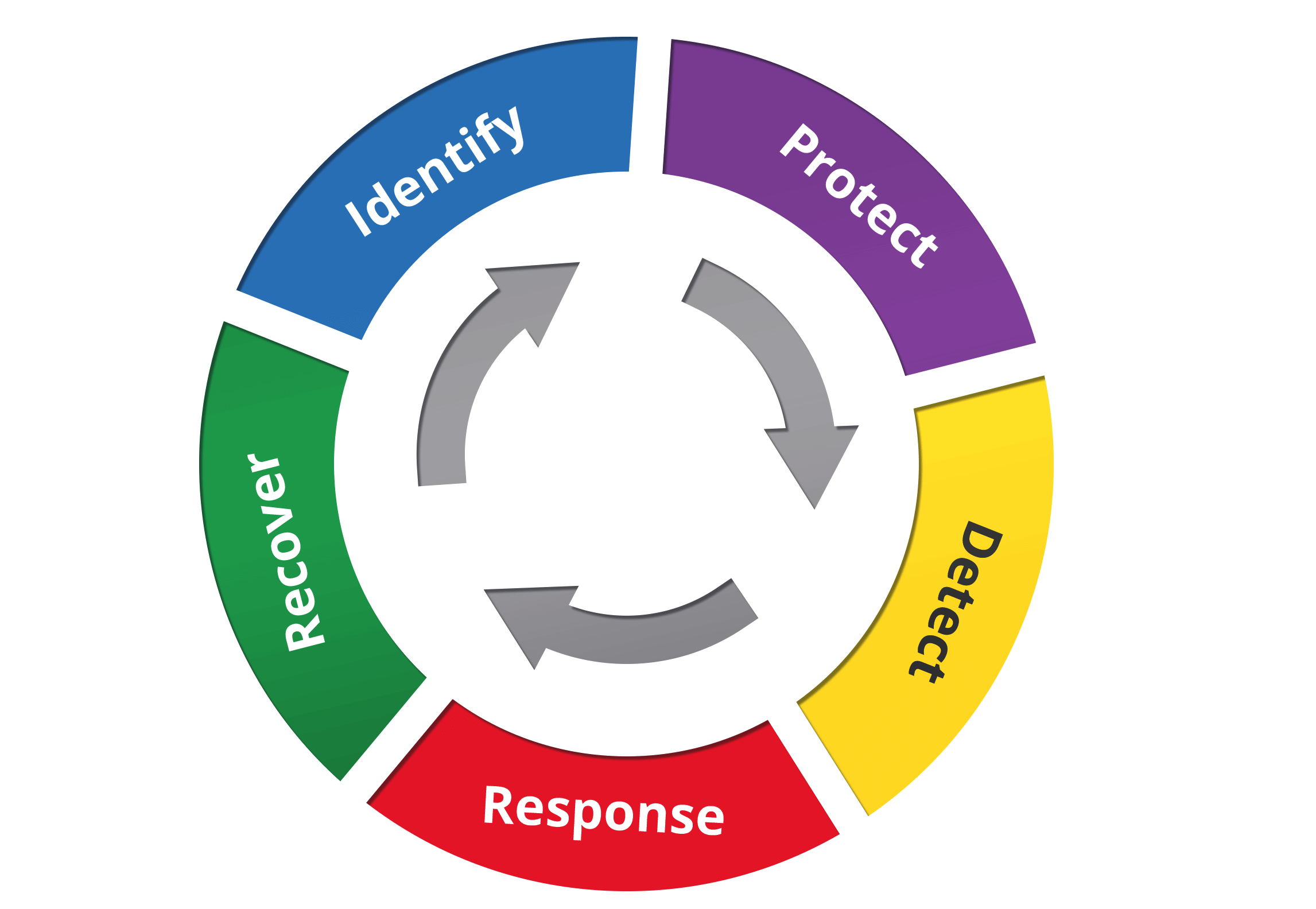
Start small. The most important—and often most difficult—step is Identify. You can’t protect what you don’t know exists.
Questions to drive the process:
- When was the last time you created an inventory?
- What is your technical stack?
- Who actually knows your technical stack?
- How many domains are in your brand’s portfolio?
- What does the supply chain look like for each digital asset?
- Which systems/services are critical dependencies?
- Where are they hosted?
- Who has access to these environments?
We don’t get hacked because platforms are inherently insecure; we’re often missing fundamentals—or complacent. Put a framework in place so every new property is introduced to the internet with clear governance and controls.
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans