We’ve been analyzing how bad actors attack WordPress and
what they do post-compromise.
In our most recent observation, the attacker modified the active theme’s functions.php and injected
17,000 SEO links. This article unpacks those links—what they were, where they pointed, and what we can learn.
Updated: 2022-08-24 — Direct links to the series:
- Part 1: How WordPress Gets Hacked in 2022 — Initial Reconnaissance
- Part 2: What Hackers Do with WordPress in 2022 — Post Hack Analysis
- Part 3: Analyzing 17,000 Spam Links on a Hacked WordPress Site
- Part 4: Hijacking a Website’s SERP Results with SEO Spam
- Part 5: Navigating 81 Layers of Encoding to Reveal the C&C
The Anatomy of 17,000 Link Injections
At first glance it looks like an attempt to signal “cornerstone” content by mass-highlighting high-value keywords and building link equity toward destination pages the attacker controls.
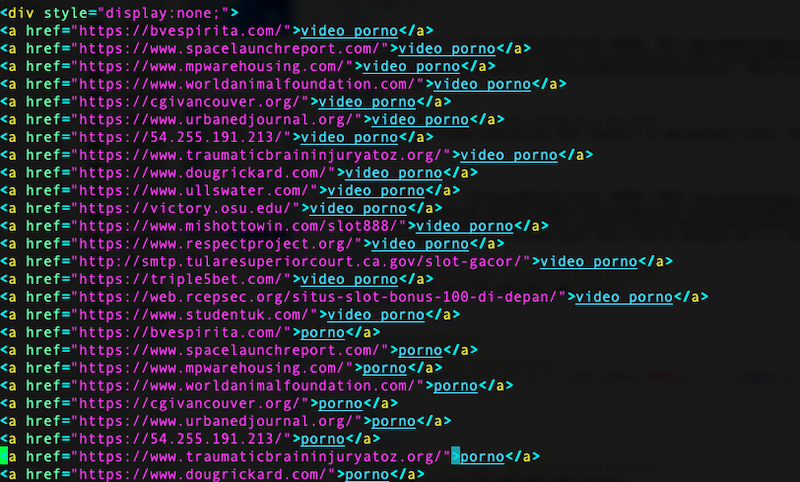
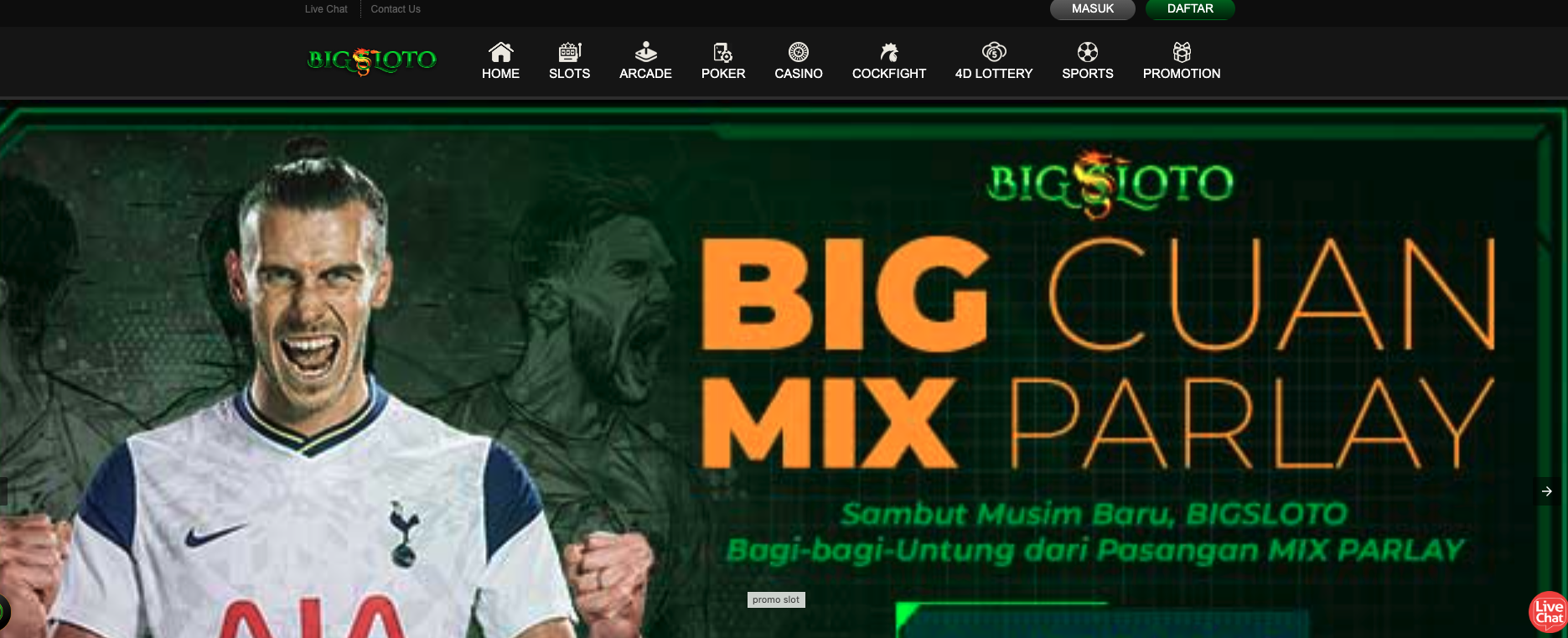
Oddly, many destinations render as casino pages when visited directly, suggesting the network is monetizing compromised properties at scale.
On closer inspection, although 17k entries were inserted, we only found 16 unique domains (each repeated exactly 1,000 times) and a single IP address pivot. Hosting/CDN footprints hint that many of these are previously compromised legitimate sites rather than attacker-owned infrastructure.
| Domain | Location | # of Instances |
|---|---|---|
| 54.255.191.213 | Amazon EC2 | 1,000 |
| bvespirita[.]com | Cloudflare | 1,000 |
| cgivancouver[.]org | Cloudflare | 1,000 |
| smtp.tularesuperiorcourt[.]ca[.]gov/slot-gacor/ | Pantheon | 1,000 |
| triple5bet[.]com | Cloudflare | 1,000 |
| victory[.]osu[.]edu | Pantheon | 1,000 |
| web[.]rcepsec[.]org/situs-slot-bonus-100-di-depan/ | CloudHost | 1,000 |
| dougrickard[.]com | Cloudflare | 1,000 |
| www[.]mishottowin[.]com/slot888/ | Cloudflare | 1,000 |
| www[.]mpwarehousing[.]com | Cloudflare | 1,000 |
| www[.]respectproject[.]org | Cloudflare | 1,000 |
| www[.]spacelaunchreport[.]com | Cloudflare | 1,000 |
| www[.]studentuk[.]com | Cloudflare | 1,000 |
| www[.]traumaticbraininjuryatoz[.]org | Cloudflare | 1,000 |
| www[.]ullswater[.]com | Cloudflare | 1,000 |
| www[.]urbanedjournal[.]org | Cloudflare | 1,000 |
| www[.]worldanimalfoundation[.]com | Cloudflare | 1,000 |
~76.5% of the domains sit behind Cloudflare. That alone isn’t conclusive (free CDN + common usage), but most domains appear to have been compromised within the past 30–45 days (per archive signals). Several attackers added spam pages under otherwise legitimate sites to delay detection.
The strategy likely aims to capitalize on high-volume queries (e.g., adult/“casino” terms) by spraying links from many hacked origins. This pattern often leads to blacklisting by search engines—and long-tail SEO damage for victims.
Trunc — SIEM & Log Management
Centralize logs, search in real time, and ship alerts that matter. Simple, fast, and affordable.
Get Started