Of all the ways a server is compromised, the access vertical continues to be the #1 vector. Whether it’s through brute-forcing weak passwords or leaked credentials, new servers see automated attacks within minutes of going live. That’s why we’re focusing on SSH. This article assumes you’re already connecting via Secure Shell (SSH) and skips basics like “don’t use FTP.”
Common SSH Hardening Tips
There are well-documented fundamentals you can enforce in sshd_config:
| # | Description |
|---|---|
| 1 | Disable password authentication (use key-based auth only). |
| 2 | Disallow direct root login. |
| 3 | Disable unused authentication mechanisms. |
| 4 | Disable unneeded features (e.g., X11Forwarding, user environment, tunneling/forwarding when not required). |
We dive deeper into each in this step-by-step guide:
Uncommon Tip: Employ an Allowlist Model
Beyond the usual hardening, one of the most effective controls is to adopt an IP allowlist for SSH: explicitly define who can access the server and block everyone else. Allowlists are typically smaller and easier to manage than constantly changing blocklists.
The challenge is remote work and dynamic IPs. To help with this, we provide an IPAuth SSH authentication module that keeps your server’s allowlist in sync with your current IP. There’s a free option and a version included with NOC.
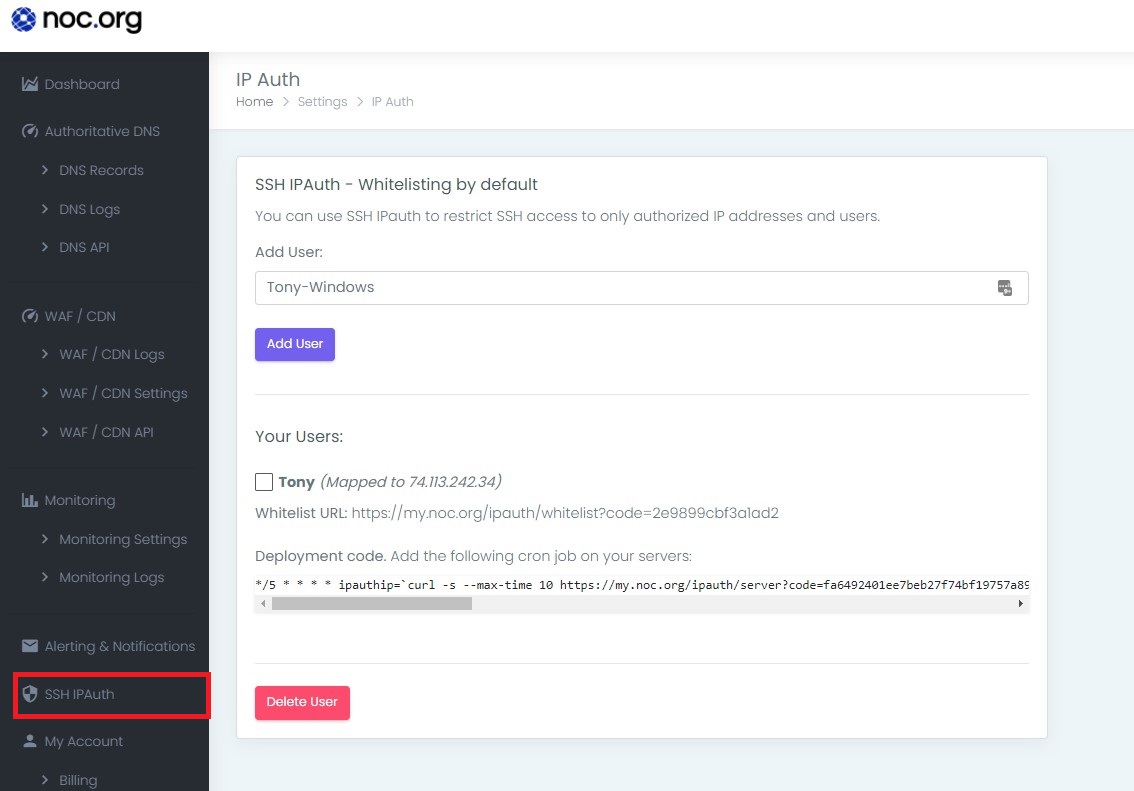
IPAuth provides two key URLs:
| Part | Explanation |
|---|---|
| Authentication URL | Used locally to capture your current IP (bookmark this). |
| Server Key URL | Queried by the server to pull your latest IP and refresh the allowlist. |
Deploy the Server Key URL on the server side; keep the Authentication URL locally. A simple cron job can hit the Authentication URL periodically (e.g., every minute or hour) and update your server when your IP changes.
Among available SSH controls, maintaining a tight allowlist has proven extremely effective at keeping bad actors out. For implementation details, see:
NOC — Authoritative DNS, CDN & WAF
Accelerate and protect your sites with global DNS, edge caching, and an always-on web application firewall.
See Plans