In our last article, How WordPress Gets Hacked in 2022 - Initial Reconnaissance, we analyzed the behaviors (TTPs) of bad actors trying to hack a vanilla WordPress deployment. Confirming our suspicions, attacks targeting access controls continue to be the #1 preferred vector by bad actors.
Analysis showed that attackers were especially interested in abusing WP-JSON and XML-RPC—WP-JSON to enumerate users and XML-RPC to brute-force authentication. The question then becomes: what happens after compromise?
This post shares what we observed while actively monitoring our honeypot.
Updated: 2022-08-24 — Direct links to the series:
- Part 1: How WordPress Gets Hacked in 2022 - Initial Reconnaissance
- Part 2: What Hackers Do with WordPress in 2022 - Post Hack Analysis
- Part 3: Analyzing 17,000 Spam Links on a Hacked WordPress Site
- Part 4: Hijacking a Website’s SERP Results with SEO SPAM
- Part 5: Navigating 81 Layers of Encoding to Reveal the C&C
Taking Control
After two weeks of waiting, we simplified the admin password to accelerate the test (the vector remains credential-stuffing/brute-force via wp-login.php / XML-RPC).
36.70.226.251 - - [21/Aug/2022:15:32:46 +0000] "GET //wp-login.php HTTP/1.1" 200 6992 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/104.0.0.0 Safari/537.36"Captured POST (custom honeypot logger):
2022-08-21 15:32:53 - 36.70.226.251 {"log":"administrator","pwd":"admin","wp-submit":"Log In","redirect_to":"https:\/\/[honeypot]\/wp-admin\/","testcookie":"1"} /wp-login.phpThey quickly navigated to install a file manager plugin:
36.70.226.251 - - [21/Aug/2022:15:33:04 +0000] "GET /wp-admin/plugin-install.php HTTP/1.1" 200 ...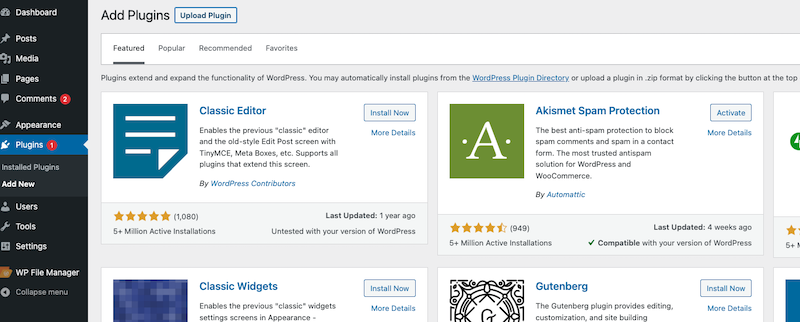
Then installed and activated it:
... "POST /wp-admin/admin-ajax.php" ... "GET /wp-admin/plugins.php?activate=true ..." Using the file manager, they uploaded three backdoors:
qiqi.php, ar.php, klee.phpThey verified access and tested execution:
GET /wp-content/qiqi.php
GET /wp-content/qiqi.php?path=/var/wwwSide Note: Importance of Testing
One backdoor failed due to deprecated PHP:
PHP Fatal error: Uncaught Error: Call to undefined function create_function() ... (removed in PHP 8)$ php -v
PHP 8.1.2 (cli) ...Deploying a Payload
After a short break (and IP change), the attacker browsed to the active theme directory and edited functions.php, posting a large payload:
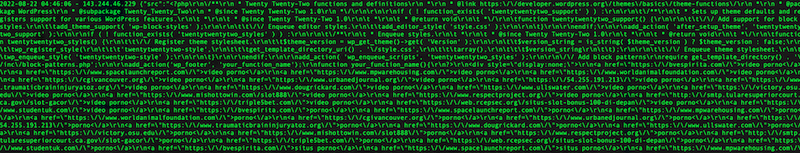
The injected code appended an off-screen block of links (SEO spam) after the PHP close tag:
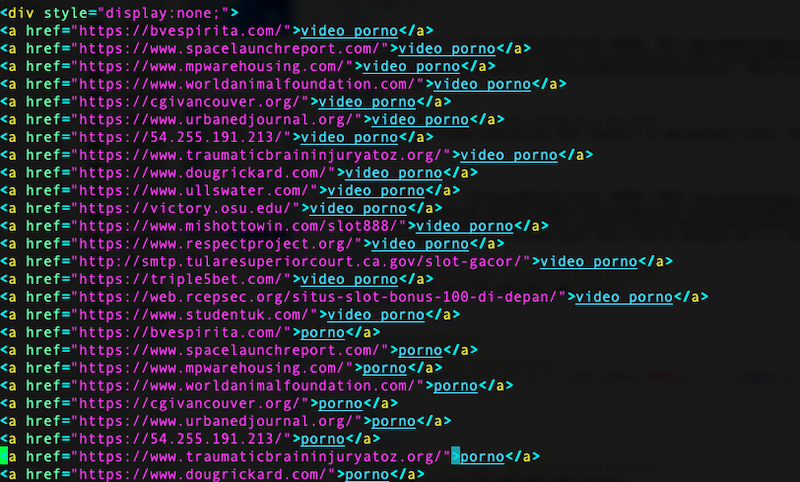
Hidden with:
<div style="display:none;">Invisible in the DOM, but obvious in page source:
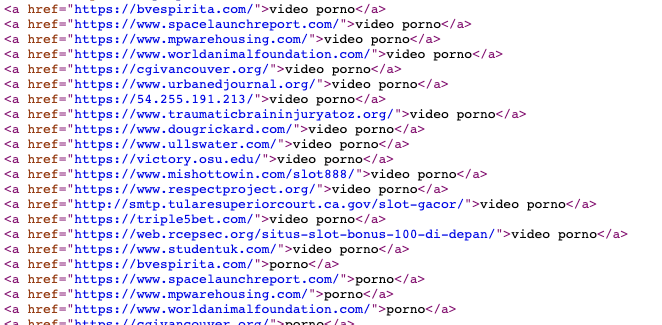
Learning From a Post-Hack Experience
Beyond credential hygiene, two hardening steps stand out:
- Block file writes from the web user (OS-level permissions, or immutable deployments).
- Disable in-dashboard file edits/installs:
define('DISALLOW_FILE_MODS', true);We’ll continue tracking additional actors and payloads in the series.
Trunc — SIEM & Log Management
Centralize logs, search in real time, and ship alerts that matter. Simple, fast, and affordable.
Get Started