We have been analyzing how bad actors attack WordPress, and what they do after they take control of a website. In our most recent article we watched as they modified a functions file for the active theme and injected it with 17,000 SEO links.
This article dives into those 17,000 links to see what they are and what we can learn from them.
**Updated: 2022-08-24: Include a more direct list of all articles related to this research:
- Part 1: How WordPress Gets Hacked in 2022 – Initial Reconnaissance
- Part 2: What Hackers Do with WordPress in 2022 – Post Hack Analysis
- Part 3: Analyzing 17,000 Spam Links on a Hacked WordPress Site
- Part 4: Hijacking a Websites SERP Results with SEO SPAM
- Part 5: Navigating 81 Layers of Encoding to Reveal the C&C
The Anatomy of 17,000 Link Injections
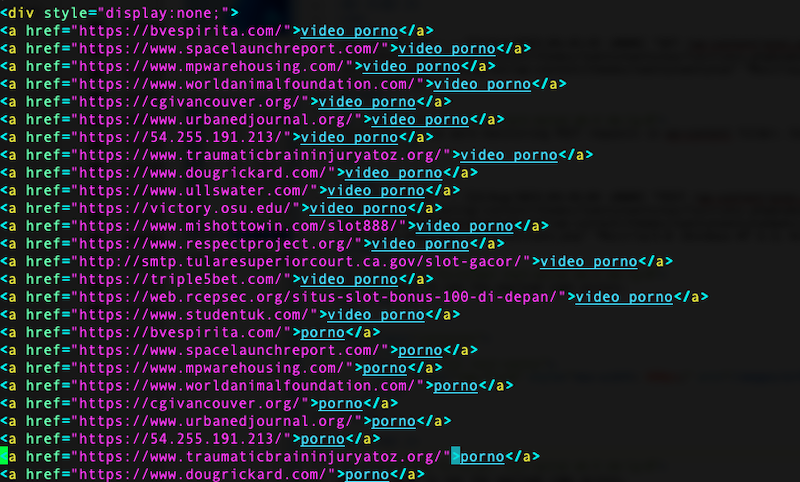
At first glance, it appears that the they are trying to trick Google into identifying cornerstone content on these domains by highlighting key words.
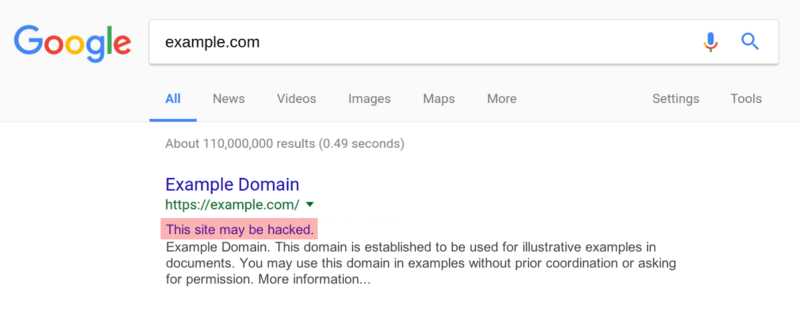
But what makes it really weird is that when you visit the hacked websites they are all Casino pages:
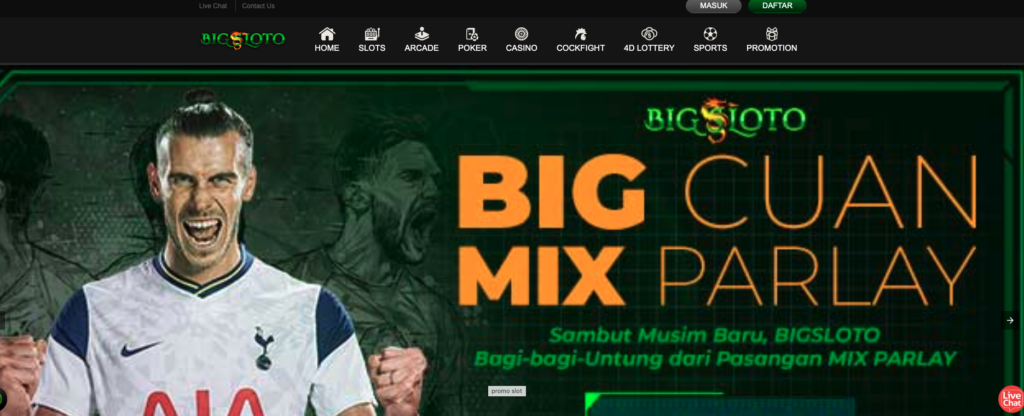
At first we were hoping that these were all malicious domains, but it turns out that a majority of them are websites that have been hacked. It also looks as if while they inserted 17k entries, there were only 16 unique domains (each listed 1,000 times exactly), and 1 IP.
| Domain | Location | Instances |
|---|---|---|
| 54.255.191.213 | Amazon EC2 | 1,000 |
| bvespirita[.]com | CloudFlare | 1,000 |
| cgivancouver[.]org | CloudFlare | 1,000 |
| smtp.tularesuperiorcourt[.]ca[.]gov/slot-gacor/ | Pantheon | 1,000 |
| triple5bet[.]com | CloudFlare | 1,000 |
| victory[.]osu[.]edu | Pantheon | 1,000 |
| web[.]rcepsec[.]org/situs-slot-bonus-100-di-depan/ | CloudHost | 1,000 |
| dougrickard[.]com | CloudFlare | 1,000 |
| www[.]mishottowin[.]com/slot888/ | CloudFlare | 1,000 |
| www[.]mpwarehousing[.]com | CloudFlare | 1,000 |
| www[.respectproject[.]org | CloudFlare | 1,000 |
| www[.]spacelaunchreport[.]com | CloudFlare | 1,000 |
| www[.]studentuk[.]com | CloudFlare | 1,000 |
| www[.]traumaticbraininjuryatoz[.]org | CloudFlare | 1,000 |
| www[.]ullswater[.]com | CloudFlare | 1,000 |
| www[.]urbanedjournal[.]org | CloudFlare | 1,000 |
| www[.]worldanimalfoundation[.]com | CloudFlare | 1,000 |
Coincidently, 76.5% of the domains were sitting behind CloudFlare. But you can’t extrapolate too much from that, they are Free CDN service and for years bad actors have used them to keep their properties up.
But, that does bring me to a different point. With exception to the IP, and triple5bet[.]com, all other domains seemed to come from organizations that had their website hacked in the past 30 – 45 days (according to archive.org).
In one instance, one domain holder gave up their main TLD and switched to another one (.com -> .org). We can’t tell if this was as a response to the hack, and just starting over, or maybe a domain expiring. Being that it’s an organization, however, they would have been able to win an argument with a registrar, so we’re leaning towards it being an easy fix to use a different TLD.
We also noticed other variations where pages were added to the main domains, leaving the main site in tact. Most likely intended to reduce the risk of being detected.
This brings us full circle to what they were trying to do with all these link injections.
Our best bet is they were trying to capitalize on key words that are ranking really high right now and directing them to these sites through the art of link backs and cornerstone content. What better keywords to target than porn, and porno, which makes up a dramatic amount of online traffic.
Needless to say, this type of injection is bound to get your website blacklisted by Google and other search engines.